Why Use File Transfer Protocols? Secure Data Transfer Tips

In today's digital age, where data is the new currency, ensuring secure and efficient data transfer is of utmost importance. File transfer protocols play a crucial role in facilitating safe and reliable data exchange between systems, networks, and individuals. These protocols offer a range of benefits, from enhanced security to improved efficiency, making them an essential tool for businesses and individuals alike.
With the ever-increasing volume of data being transmitted over the internet, the need for robust and secure file transfer solutions has become imperative. Whether it's sharing sensitive business documents, transferring large media files, or collaborating on projects across different locations, file transfer protocols provide a reliable and controlled environment for data exchange.
Understanding File Transfer Protocols

File transfer protocols are a set of rules and conventions that govern the secure and efficient transfer of data between systems. These protocols define the communication process, ensuring that data is transmitted accurately and securely, regardless of the underlying network infrastructure.
One of the key advantages of using file transfer protocols is their ability to provide a secure environment for data exchange. These protocols employ encryption techniques to protect data during transmission, ensuring that sensitive information remains confidential and secure. By encrypting data, file transfer protocols mitigate the risks associated with data breaches and unauthorized access.
Furthermore, file transfer protocols offer a high level of reliability and efficiency. They are designed to handle large volumes of data, ensuring smooth and uninterrupted transfers. These protocols also incorporate error-checking mechanisms, which help detect and correct any data corruption or transmission errors, thus minimizing the chances of data loss or corruption.
Benefits of File Transfer Protocols

Enhanced Security
File transfer protocols prioritize security, employing advanced encryption algorithms to safeguard data during transmission. By encrypting data, these protocols protect sensitive information from unauthorized access, interception, or tampering. This is particularly crucial when transferring confidential business documents, personal records, or any data that requires a high level of privacy and security.
Additionally, file transfer protocols often include authentication mechanisms, ensuring that only authorized users can access and transfer data. This adds an extra layer of security, preventing unauthorized individuals from gaining access to sensitive information. By combining encryption and authentication, file transfer protocols provide a robust and secure environment for data exchange.
Efficient Data Transfer
File transfer protocols are designed to optimize data transfer, ensuring efficient and timely delivery. These protocols utilize advanced techniques such as compression, parallel data streaming, and intelligent file segmentation to enhance transfer speeds and minimize network congestion. As a result, businesses and individuals can transfer large files or multiple files simultaneously without experiencing significant delays.
Moreover, file transfer protocols offer reliable error detection and recovery mechanisms. In the event of transmission errors or network disruptions, these protocols can automatically detect and correct errors, ensuring the integrity of the transferred data. This feature is particularly valuable when dealing with critical or time-sensitive data, as it minimizes the risk of data loss or corruption.
Automated and Scheduled Transfers
File transfer protocols provide the flexibility to automate and schedule data transfers. This feature is highly beneficial for businesses that require regular data backups, updates, or synchronization between different systems or locations. By automating the transfer process, organizations can streamline their data management operations, reduce manual errors, and ensure timely and consistent data transfers.
Additionally, scheduled transfers allow businesses to optimize their network resources and minimize the impact on network performance during peak hours. By offloading data transfers to off-peak hours, organizations can ensure efficient and uninterrupted network operations, thus improving overall network efficiency and user experience.
Choosing the Right File Transfer Protocol
When selecting a file transfer protocol, it's essential to consider the specific requirements and constraints of your data transfer needs. Different protocols offer varying levels of security, performance, and compatibility, so choosing the right one is crucial for a successful and secure data transfer experience.
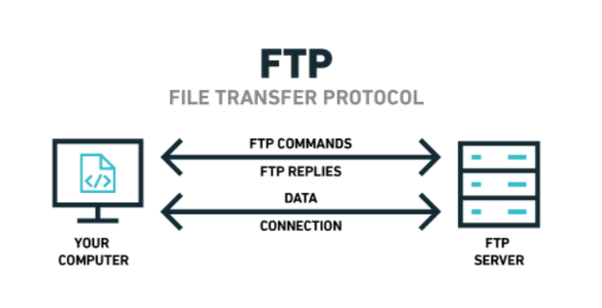
Some of the commonly used file transfer protocols include FTP (File Transfer Protocol), SFTP (Secure File Transfer Protocol), FTPS (FTP over SSL/TLS), and HTTPS (HTTP over SSL/TLS). Each protocol has its unique features and use cases, and the choice depends on factors such as the level of security required, the size and nature of the data being transferred, and the network infrastructure in place.
For instance, FTP is a widely used protocol that offers basic security features, making it suitable for transferring non-sensitive data. On the other hand, SFTP and FTPS provide higher levels of security through encryption and authentication, making them ideal for transferring sensitive information. HTTPS, being a secure version of HTTP, is commonly used for web-based file transfers and is particularly useful for transferring data over the internet.
Implementing Secure Data Transfer Practices
To ensure secure data transfer, it's essential to follow best practices and implement robust security measures. Here are some key tips to enhance the security and efficiency of your file transfer processes:
- Use Strong Passwords: Ensure that all user accounts and access points are protected with strong, unique passwords. Avoid using easily guessable passwords or sharing passwords across multiple accounts.
- Enable Two-Factor Authentication: Implement two-factor authentication (2FA) to add an extra layer of security. This requires users to provide a second form of authentication, such as a code sent to their mobile device, in addition to their password.
- Regularly Update Software: Keep your file transfer software and operating systems up to date. Software updates often include security patches and bug fixes, which help protect against known vulnerabilities and potential exploits.
- Limit Access: Restrict access to sensitive data and file transfer systems to authorized users only. Implement role-based access controls and permissions to ensure that only those who need access can transfer or view specific files.
- Monitor and Audit Transfers: Implement monitoring and auditing mechanisms to track and record all file transfer activities. This helps identify any suspicious or unauthorized transfers and allows for timely investigation and response.
- Use Encryption: Always encrypt data during transfer to protect it from unauthorized access or interception. Choose a file transfer protocol that supports strong encryption algorithms and ensure that encryption is enabled by default.
- Secure Transfer Endpoints: Ensure that both the sending and receiving endpoints are secure. This includes securing the network infrastructure, implementing firewall rules, and using secure network protocols such as HTTPS or SSH.
By following these best practices and implementing robust security measures, you can significantly enhance the security and efficiency of your file transfer processes. Remember, data security is an ongoing process, and it's essential to stay updated with the latest security practices and technologies to protect your sensitive information.
The Future of File Transfer Protocols
As technology continues to advance, file transfer protocols are also evolving to meet the growing demands and challenges of data transfer. With the increasing adoption of cloud computing, the Internet of Things (IoT), and big data analytics, file transfer protocols are being optimized to handle larger data volumes, faster transfer speeds, and more complex data formats.
Furthermore, with the rise of remote work and distributed teams, the need for secure and efficient file transfer solutions has become more critical than ever. File transfer protocols are being adapted to support collaboration and real-time data sharing, enabling seamless communication and data exchange between team members located in different parts of the world.
In the future, we can expect to see further advancements in file transfer protocols, including improved encryption algorithms, enhanced security features, and better integration with cloud-based storage and collaboration platforms. These developments will continue to shape the way data is transferred, ensuring a secure and efficient data exchange environment for businesses and individuals alike.
What is the difference between FTP and SFTP?
+FTP (File Transfer Protocol) and SFTP (Secure File Transfer Protocol) are both file transfer protocols, but they differ in their security features. FTP is a basic protocol that does not encrypt data during transfer, making it less secure for sensitive data. SFTP, on the other hand, provides encryption and authentication, ensuring a more secure environment for data exchange.
How can I ensure the security of my file transfers over public Wi-Fi networks?
+When transferring files over public Wi-Fi networks, it’s crucial to use a secure file transfer protocol such as SFTP or FTPS. These protocols encrypt data during transfer, protecting it from potential interception or unauthorized access. Additionally, it’s recommended to use a virtual private network (VPN) to establish a secure connection and further enhance the security of your file transfers.
Are there any file size limitations when using file transfer protocols?
+File size limitations can vary depending on the file transfer protocol and the underlying network infrastructure. Some protocols, such as FTP, may have limitations on the maximum file size that can be transferred. However, many modern file transfer protocols, like SFTP or FTPS, are designed to handle larger file sizes and can accommodate multiple file transfers simultaneously.
