What Data Does The Hipaa Security Rule Protect? Your Privacy Guide

The Health Insurance Portability and Accountability Act (HIPAA) is a crucial piece of legislation in the United States that aims to protect the privacy and security of individuals' health information. Enacted in 1996, HIPAA introduced standards and regulations to safeguard sensitive health data, ensuring that individuals' personal and medical details remain confidential and secure. This article will delve into the specific data covered by the HIPAA Security Rule, exploring its scope, key provisions, and the measures in place to protect individuals' privacy.
Understanding the HIPAA Security Rule

The HIPAA Security Rule is a set of national standards designed to protect individuals’ electronic personal health information (e-PHI) that is created, received, used, or maintained by a covered entity. Covered entities include healthcare providers, health plans, and healthcare clearinghouses. The rule outlines administrative, physical, and technical safeguards that must be implemented to ensure the confidentiality, integrity, and availability of e-PHI.
Administrative Safeguards
Administrative safeguards focus on the policies and procedures that covered entities must have in place to manage the security of e-PHI. This includes developing and implementing a security management process, conducting regular risk analyses, and implementing appropriate security measures based on the outcomes of these analyses. Covered entities must also establish policies and procedures to address security incidents and train their workforce on security awareness and compliance.
Physical Safeguards
Physical safeguards are designed to protect the physical security of e-PHI and the facilities where it is stored. This includes implementing access controls to restrict physical access to e-PHI, implementing procedures for safeguarding e-PHI during transmission, and ensuring the proper disposal of e-PHI media to prevent unauthorized access.
Technical Safeguards
Technical safeguards involve the use of technology to protect e-PHI. This includes implementing access controls to restrict unauthorized access to e-PHI, encrypting e-PHI during transmission and storage, implementing procedures to verify the identity of individuals accessing e-PHI, and implementing audit controls to track access to e-PHI.
Data Covered by the HIPAA Security Rule

The HIPAA Security Rule applies to a broad range of data that is considered electronic protected health information (e-PHI). Here are some key categories of data protected by the rule:
Demographic Information
HIPAA safeguards individuals’ demographic data, including names, addresses, dates of birth, Social Security numbers, and other unique identifiers. This information is often used to identify and locate individuals, making it a prime target for identity theft and fraud.
Medical Records
The security rule protects individuals’ medical records, which contain detailed information about their health status, diagnoses, treatments, and medical histories. These records may include physician notes, laboratory results, imaging reports, and prescription details. Protecting medical records is crucial to maintaining patient confidentiality and ensuring accurate medical care.
Billing and Payment Information
HIPAA also covers billing and payment information, such as insurance details, payment history, and financial records related to healthcare services. This information is sensitive as it can reveal an individual’s financial status and healthcare utilization patterns.
Communication and Contact Details
The security rule extends to individuals’ communication and contact details, including phone numbers, email addresses, and fax numbers. Protecting this information is essential to prevent unauthorized access to sensitive health-related communications.
Genetic and Biometric Data
With the advancement of technology, HIPAA now covers genetic and biometric data. Genetic information includes an individual’s DNA sequence, genetic test results, and family medical history. Biometric data refers to unique biological characteristics, such as fingerprints, retinal scans, and voice patterns, which can be used for identification and authentication purposes.
Electronic Health Records (EHRs)
EHRs have become a common tool in modern healthcare, and HIPAA ensures the security of these digital records. EHRs contain a wealth of information, including patient demographics, medical histories, laboratory results, medications, and treatment plans. Protecting EHRs is vital to maintaining the integrity and confidentiality of patient data.
Telehealth and Remote Monitoring Data
As telehealth and remote monitoring become increasingly popular, HIPAA addresses the security of data transmitted and stored during these interactions. This includes video consultations, remote patient monitoring devices, and mobile health applications. Ensuring the security of telehealth data is crucial to protecting patient privacy and maintaining the trust of individuals who rely on these services.
Measures to Protect Data under HIPAA
The HIPAA Security Rule outlines several measures that covered entities must implement to protect e-PHI. These measures include:
- Access Controls: Implementing policies and procedures to restrict access to e-PHI to authorized individuals only.
- Encryption: Using encryption technologies to protect e-PHI during transmission and storage, ensuring that only authorized individuals can access the data.
- Audit Controls: Implementing mechanisms to track and monitor access to e-PHI, helping to identify potential security breaches or unauthorized access.
- Risk Management: Conducting regular risk assessments to identify vulnerabilities and implementing appropriate security measures to mitigate those risks.
- Workforce Training: Providing ongoing training and education to employees on security awareness and HIPAA compliance to ensure they understand their roles in protecting e-PHI.
Enforcement and Penalties
The Department of Health and Human Services’ Office for Civil Rights (OCR) is responsible for enforcing HIPAA regulations. Covered entities that fail to comply with the HIPAA Security Rule may face penalties, which can include financial fines and corrective action plans. The severity of the penalties depends on the nature and extent of the violation, as well as the entity’s history of compliance.
Future Implications and Advancements
As technology continues to evolve, the protection of health information becomes increasingly complex. The HIPAA Security Rule must adapt to address emerging threats and challenges. Some key future implications and advancements include:
- Artificial Intelligence (AI) and Machine Learning: AI and machine learning technologies are being used to analyze and interpret health data. Ensuring the security and privacy of data used in these advanced analytics is a critical area of focus.
- Cloud Computing: With the rise of cloud-based healthcare solutions, covered entities must ensure that e-PHI stored in the cloud is protected from unauthorized access and data breaches.
- Mobile Health (mHealth) Apps: mHealth apps are becoming popular tools for individuals to manage their health and communicate with healthcare providers. Developing secure and privacy-preserving mHealth solutions is essential to protecting user data.
- Blockchain Technology: Blockchain has the potential to revolutionize healthcare data management by providing a secure and tamper-proof way to store and share health information. Exploring the use of blockchain in healthcare could enhance data security and privacy.
The HIPAA Security Rule plays a vital role in safeguarding individuals' health information in the digital age. By implementing robust security measures and staying abreast of technological advancements, covered entities can ensure the confidentiality, integrity, and availability of e-PHI. As healthcare continues to embrace digital transformation, maintaining a strong focus on data protection and privacy will be essential to building trust and ensuring the well-being of patients.
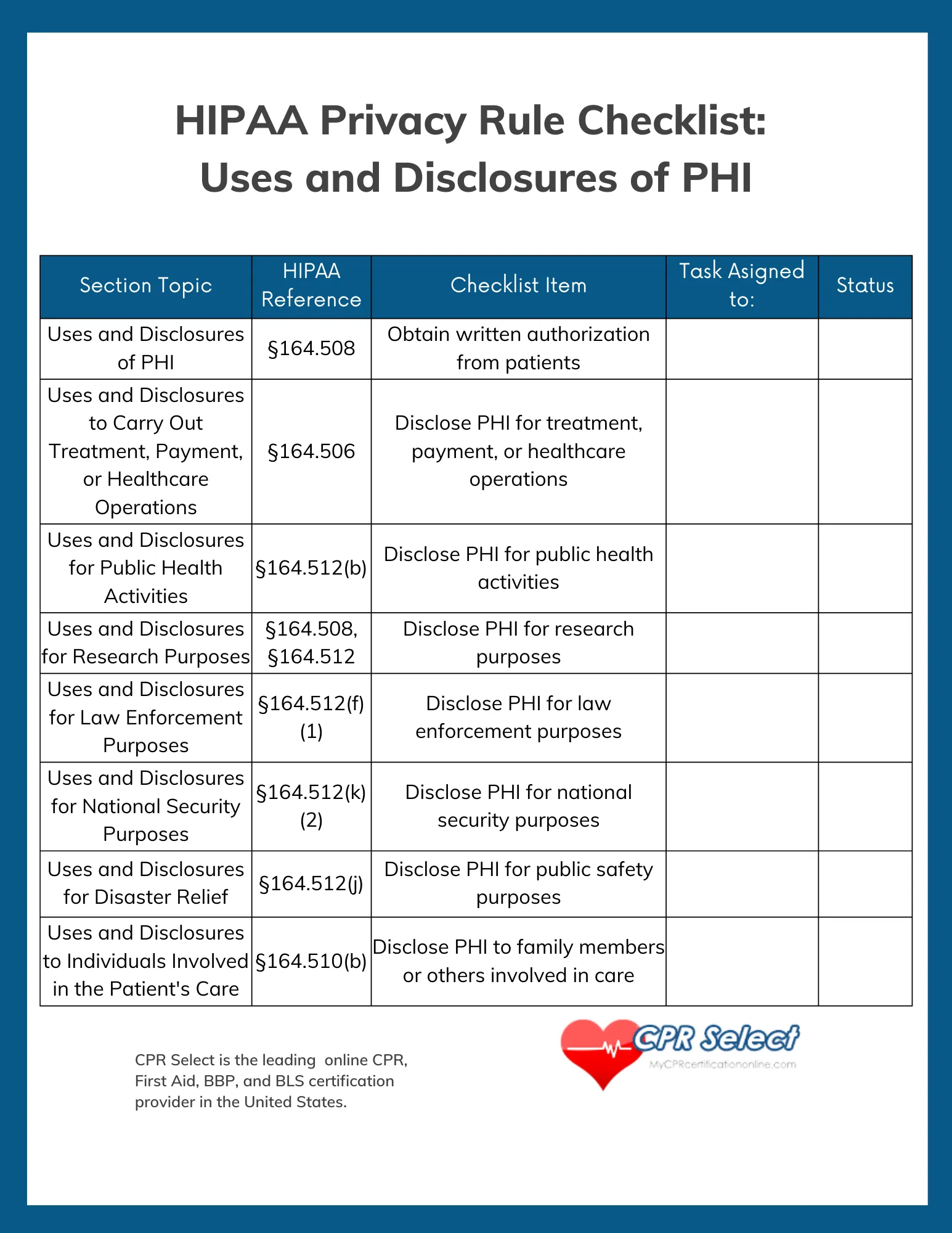
What are the key differences between the HIPAA Privacy Rule and the Security Rule?
+The HIPAA Privacy Rule focuses on the appropriate use and disclosure of protected health information (PHI), while the Security Rule specifically addresses the protection of electronic PHI (e-PHI). The Privacy Rule sets standards for obtaining patient consent, using and disclosing PHI, and providing individuals with access to their health information. The Security Rule, on the other hand, establishes technical, physical, and administrative safeguards to protect e-PHI from unauthorized access, use, disclosure, and modification.
Are all healthcare providers required to comply with the HIPAA Security Rule?
+Yes, the HIPAA Security Rule applies to all covered entities, including healthcare providers, health plans, and healthcare clearinghouses. These entities must implement the necessary safeguards to protect e-PHI. Business associates of covered entities, such as third-party service providers, are also required to comply with the Security Rule when they create, receive, maintain, or transmit e-PHI on behalf of covered entities.
What are some best practices for securing e-PHI under the HIPAA Security Rule?
+To ensure compliance with the HIPAA Security Rule, covered entities should implement the following best practices: conduct regular risk assessments, implement strong access controls, encrypt e-PHI during transmission and storage, use secure communication channels, regularly update security measures, provide comprehensive security awareness training to employees, and establish incident response plans to address security breaches promptly.


