Secure File Sharing: Master The Art Of Safe Collaboration
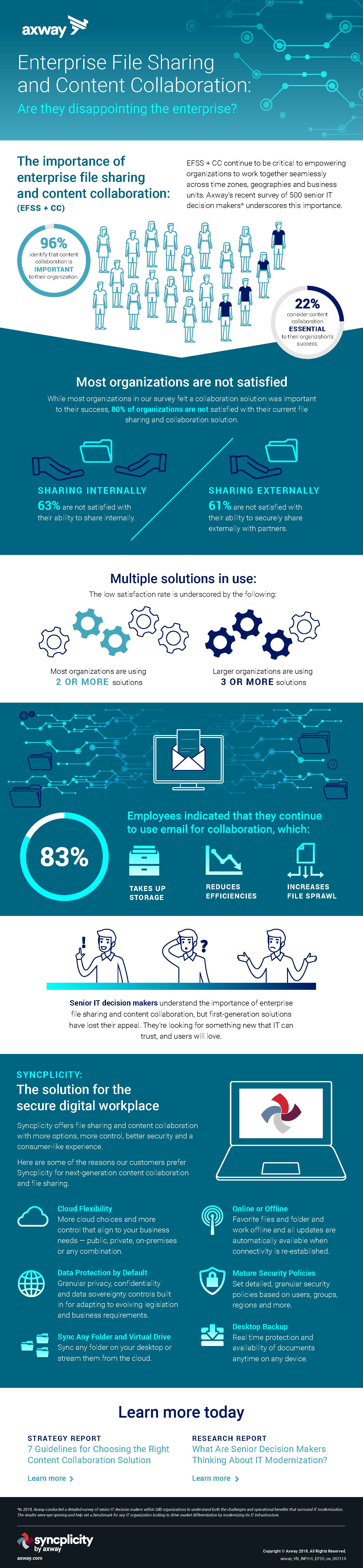
In today's digital age, collaboration and information sharing are essential for businesses and individuals alike. However, with an increasing number of cyber threats and data breaches, ensuring the security of shared files has become a critical concern. This comprehensive guide aims to equip you with the knowledge and tools to master the art of secure file sharing, empowering you to collaborate safely and protect sensitive information.
Understanding the Risks of File Sharing

File sharing, when not properly secured, can expose your data to a range of threats. From unauthorized access and data breaches to malware infections and identity theft, the consequences can be severe. Understanding these risks is the first step towards implementing effective security measures.
Common File Sharing Risks
- Unencrypted Data: Sharing files without encryption leaves them vulnerable to interception and theft.
- Phishing Attacks: Malicious actors may target shared files to gain access to sensitive information.
- Malware Infiltration: Shared files can be used to distribute malware, compromising the security of your systems.
- Data Loss: Inadequate security measures can lead to accidental data loss or deletion.
Best Practices for Secure File Sharing
To mitigate these risks, it’s crucial to follow best practices for secure file sharing. Here are some essential guidelines to consider:
- Use Secure Platforms: Opt for reputable file-sharing platforms that offer end-to-end encryption and robust security features.
- Implement Access Controls: Restrict file access to authorized individuals only, and consider using multi-factor authentication for added security.
- Encrypt Sensitive Data: Always encrypt sensitive information before sharing, ensuring that even if intercepted, the data remains unreadable.
- Regularly Update Software: Keep your file-sharing tools and security software up to date to patch any vulnerabilities.
- Educate Users: Train your team on secure file-sharing practices to prevent accidental data exposure.
Choosing the Right File Sharing Platform

Selecting the appropriate file-sharing platform is crucial for ensuring the security and efficiency of your collaboration. Here’s a closer look at some key considerations when choosing a platform:
Security Features
The security features offered by a file-sharing platform are paramount. Look for platforms that provide:
- End-to-End Encryption: This ensures that only the intended recipient can access and decrypt the shared files.
- Data Loss Prevention (DLP): DLP tools help prevent accidental or unauthorized data sharing, protecting sensitive information.
- Intrusion Detection and Prevention: These systems detect and block potential threats, enhancing the overall security of the platform.
User-Friendly Interface
A user-friendly interface is essential for efficient collaboration. Opt for platforms that offer:
- Intuitive File Management: Easy navigation and organization of files, making it simple to locate and share documents.
- Real-Time Collaboration: Features like simultaneous editing and version control facilitate efficient teamwork.
- Mobile Accessibility: Ensure the platform is accessible across devices, allowing users to collaborate on the go.
Scalability and Flexibility
Consider the platform’s ability to scale with your business needs. Look for:
- Customizable Plans: Choose a platform that offers flexible pricing and features to accommodate your team's size and requirements.
- Integration Capabilities: Integrate the file-sharing platform with your existing tools and systems for seamless collaboration.
- API Access: For advanced users, API access allows for custom integration and automation, enhancing productivity.
Implementing Secure File Transfer Protocols
To further enhance the security of your file sharing, it’s essential to implement secure transfer protocols. These protocols ensure that your data remains protected during transit.
Secure Transfer Protocols
Here are some commonly used secure transfer protocols and their benefits:
- SFTP (SSH File Transfer Protocol): SFTP provides secure file transfer over an SSH connection, ensuring encryption and authentication.
- FTPS (FTP over SSL/TLS): FTPS offers encryption and authentication, protecting your data during transfer.
- HTTPS (HTTP Secure): HTTPS is widely used for secure web browsing and file sharing, ensuring encrypted data transmission.
Configuring Secure Transfer Settings
To implement secure transfer protocols effectively, consider the following configuration tips:
- Use Strong Passwords: Ensure that all user accounts have strong, unique passwords to prevent unauthorized access.
- Enable Two-Factor Authentication: Add an extra layer of security by requiring users to provide a code from their mobile device.
- Regularly Update Credentials: Change passwords and access credentials periodically to minimize the risk of unauthorized access.
Data Encryption: The Key to Secure File Sharing
Data encryption is a critical component of secure file sharing. By encrypting your files, you ensure that even if they are intercepted, the data remains unreadable and protected.
Types of Encryption
There are two main types of encryption used in file sharing:
- Symmetric Encryption: This method uses a single key for both encryption and decryption, making it faster but less secure for large-scale sharing.
- Asymmetric Encryption: Asymmetric encryption uses a pair of keys - a public key for encryption and a private key for decryption. This provides stronger security but can be slower.
Best Practices for Encryption
When implementing encryption for file sharing, consider the following best practices:
- Use Strong Encryption Algorithms: Opt for proven encryption algorithms like AES (Advanced Encryption Standard) to ensure the highest level of security.
- Encrypt at Rest and in Transit: Ensure that your files are encrypted not only during transfer but also when stored on servers or devices.
- Manage Encryption Keys Securely: Store and manage encryption keys in a secure, centralized location to prevent unauthorized access.
Collaborating Safely: Tips for Secure File Sharing

Now that we’ve covered the technical aspects of secure file sharing, let’s explore some practical tips to ensure safe collaboration.
User Training and Awareness
Educating your team on secure file-sharing practices is crucial. Conduct regular training sessions to cover topics like:
- Identifying Phishing Attempts: Teach users to recognize and report potential phishing attacks.
- Secure Password Management: Emphasize the importance of strong, unique passwords and regular updates.
- Secure File Handling: Provide guidelines on how to securely handle, store, and share files.
Establishing File Sharing Policies
Implement clear file-sharing policies within your organization. These policies should cover:
- Authorized File Sharing Platforms: Specify which platforms are approved for use and their intended purposes.
- Data Classification: Define the sensitivity levels of different types of data and the appropriate sharing protocols.
- Incident Reporting: Establish a process for reporting and responding to security incidents or data breaches.
Regular Security Audits
Conduct regular security audits to identify and address potential vulnerabilities. These audits should include:
- Network Scans: Scan your network for potential weaknesses and unauthorized access points.
- Password Audits: Regularly review and update user passwords to maintain security.
- Security Awareness Assessments: Test your team's awareness and response to potential security threats.
Future Trends in Secure File Sharing
The field of secure file sharing is constantly evolving, with new technologies and innovations shaping the landscape. Here’s a glimpse into some of the future trends:
Blockchain for Secure File Sharing
Blockchain technology is gaining traction in secure file sharing due to its decentralized nature and immutability. By using blockchain, file-sharing platforms can offer enhanced security, transparency, and auditability.
AI-Powered Security
Artificial Intelligence (AI) is being leveraged to enhance file-sharing security. AI-powered tools can detect and respond to potential threats in real-time, improving overall security.
Quantum-Safe Encryption
As quantum computing advances, the need for quantum-safe encryption becomes more critical. Quantum-safe encryption algorithms can withstand attacks from quantum computers, ensuring long-term data security.
Conclusion
Mastering the art of secure file sharing is essential for businesses and individuals alike. By implementing the best practices, choosing secure platforms, and staying updated with emerging technologies, you can ensure that your collaboration remains safe and your data protected. Remember, secure file sharing is a continuous process, requiring regular updates, user education, and a proactive approach to security.
How can I choose the right file-sharing platform for my business?
+When selecting a file-sharing platform, consider your specific needs. Look for platforms with robust security features, user-friendly interfaces, and scalability. Evaluate their encryption protocols, access controls, and integration capabilities. Additionally, consider the platform’s reputation and customer support to ensure a reliable and secure experience.
What are the benefits of using encryption for file sharing?
+Encryption is a critical component of secure file sharing. It ensures that even if your files are intercepted during transit or stored on an unsecured server, the data remains unreadable and protected. By using strong encryption algorithms, you can safeguard sensitive information and maintain the confidentiality of your data.
How can I train my team on secure file-sharing practices?
+User training is essential for secure file sharing. Conduct regular training sessions to educate your team on identifying phishing attempts, managing passwords securely, and handling files safely. Provide clear guidelines and policies, and encourage a culture of security awareness within your organization.


