12 Ways To Securely Share Documents Online
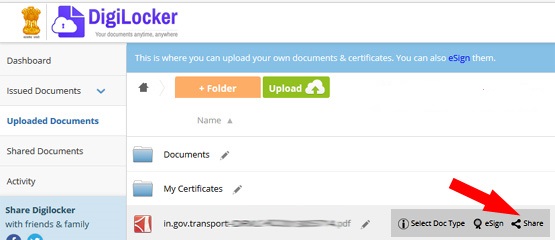
In today's digital age, sharing documents online has become an integral part of our personal and professional lives. However, with the increasing risks of data breaches and cyber threats, it is crucial to prioritize document security. Whether you're collaborating with colleagues, sharing sensitive information with clients, or simply sending personal files, implementing robust security measures is essential. In this comprehensive guide, we will explore 12 effective ways to securely share documents online, ensuring your data remains protected.
1. Choose a Reputable Cloud Storage Service

Selecting a reliable cloud storage service is the foundation of secure document sharing. Look for established providers with a strong track record in data security. Choose a service that offers robust encryption protocols, two-factor authentication, and access control features. Services like Google Drive, Dropbox, and Microsoft OneDrive provide robust security measures and easy collaboration tools.
Example: Google Drive’s Security Features
Google Drive, for instance, offers end-to-end encryption, allowing only authorized users to access the content. It also provides options for setting file permissions, ensuring that only specific individuals or groups can view, edit, or share documents.
| Cloud Storage Service | Security Features |
|---|---|
| Google Drive | End-to-end encryption, two-factor authentication, access control |
| Dropbox | AES-256 encryption, two-step verification, remote wipe |
| Microsoft OneDrive | BitLocker encryption, multi-factor authentication, file recovery |

2. Utilize Encryption and Password Protection

Encrypting your documents adds an extra layer of security. Use encryption software to protect sensitive files before sharing them online. Additionally, consider password-protecting your documents to ensure only authorized individuals can access the content. Tools like 7-Zip or WinZip offer encryption options for various file formats.
Real-World Example: Password-Protected PDFs
When sharing confidential reports with clients, you can create password-protected PDFs. Adobe Acrobat, for instance, allows you to set passwords for opening, editing, or printing the document, ensuring that only authorized individuals can access the information.
3. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds an extra step to the login process, significantly enhancing security. By requiring a second form of verification, such as a code sent to your mobile device, you add an additional layer of protection against unauthorized access. Most cloud storage services and collaboration platforms offer 2FA as an option.
Benefits of Two-Factor Authentication
- Prevents unauthorized access, even if passwords are compromised.
- Provides an extra layer of security for your online accounts.
- Notifies you of login attempts, allowing you to take immediate action.
4. Set Up Access Controls and Permissions
Fine-tune access controls and permissions to ensure only authorized individuals can view or edit your shared documents. Most cloud storage services allow you to set different levels of access, such as read-only, edit, or full control. By carefully managing permissions, you can control who has access to your sensitive information.
Best Practices for Access Controls
- Grant the minimum level of access required for each user or group.
- Regularly review and update access permissions to ensure they align with your needs.
- Consider using unique access keys or tokens for added security.
5. Implement Digital Signatures and Verification
Digital signatures provide an extra level of assurance when sharing documents. They ensure the integrity and authenticity of the content, verifying the sender’s identity. Use digital signature software or built-in features in cloud storage services to add digital signatures to your documents.
Digital Signature Verification Process
- The sender digitally signs the document using their private key.
- The recipient verifies the signature using the sender’s public key.
- If the signature is valid, the document’s integrity and sender’s identity are confirmed.
6. Utilize Secure File Transfer Protocols (SFTP)
SFTP (Secure File Transfer Protocol) provides a secure way to transfer files over the internet. It encrypts the data during transit, ensuring that even if the files are intercepted, they remain unreadable without the decryption key. SFTP is particularly useful when transferring large or sensitive files.
Setting Up SFTP for Secure File Transfer
- Install an SFTP client on your device, such as FileZilla or WinSCP.
- Connect to the SFTP server using your login credentials.
- Upload or download files securely, ensuring data protection.
7. Regularly Update and Patch Software
Keeping your software up to date is crucial for maintaining security. Software updates often include security patches that address vulnerabilities and fix potential exploits. Ensure that your operating system, web browsers, and document sharing applications are regularly updated to minimize the risk of security breaches.
Benefits of Regular Software Updates
- Fixes security vulnerabilities and exploits.
- Improves overall software performance and stability.
- Provides access to new features and enhancements.
8. Use Virtual Private Networks (VPNs) for Secure Connections
A VPN creates a secure, encrypted connection between your device and the internet. It masks your IP address and encrypts your data, ensuring privacy and security while sharing documents online. VPNs are particularly useful when accessing sensitive information over public Wi-Fi networks.
Choosing the Right VPN Service
- Look for VPNs with strong encryption protocols, such as AES-256.
- Consider VPNs with a no-logs policy to ensure your online activities remain private.
- Choose a VPN with a wide range of server locations for better connectivity.
9. Employ End-to-End Encryption for Maximum Security
End-to-end encryption ensures that only the sender and recipient can access the content of a message or document. The data is encrypted on the sender’s device and can only be decrypted by the intended recipient. This provides the highest level of security for sensitive information.
Example: Signal’s End-to-End Encryption
Signal, a popular messaging app, uses end-to-end encryption to protect user communications. Even if the messages are intercepted, they remain unreadable without the recipient’s private key.
10. Educate Yourself and Your Team on Security Best Practices
Security is a shared responsibility. Educate yourself and your team on security best practices to minimize the risk of data breaches. Stay informed about the latest security threats and learn how to recognize and avoid potential risks when sharing documents online.
Key Security Tips to Remember
- Never share sensitive information over unsecured networks.
- Be cautious of phishing attempts and suspicious emails.
- Use strong, unique passwords for all your accounts.
11. Regularly Back Up Your Data
Backing up your data is crucial to ensure business continuity and protect against data loss. Regularly back up your documents to a secure, off-site location or use cloud storage services with built-in backup features. This way, even if your primary storage is compromised, you have a backup to rely on.
Benefits of Regular Data Backups
- Protects against data loss due to hardware failures or disasters.
- Ensures business continuity and quick recovery.
- Provides a safe haven for your critical documents and data.
12. Monitor and Audit Shared Documents
Regularly monitor and audit your shared documents to identify potential security breaches or unauthorized access attempts. Most cloud storage services provide activity logs and audit trails, allowing you to track who accessed your files and when. This helps you identify and address any security concerns promptly.
Best Practices for Monitoring Shared Documents
- Set up alerts for suspicious activities or unauthorized access attempts.
- Review access logs regularly to identify any anomalies.
- Implement access reviews to ensure permissions remain up-to-date.
How often should I update my security measures?
+It is recommended to review and update your security measures at least once a year. However, if there are significant changes in your team, new security threats emerge, or you notice any suspicious activities, it’s crucial to update your security protocols immediately.
What are the signs of a potential security breach?
+Signs of a potential security breach include unexpected changes in file permissions, unauthorized access attempts, unusual login activities, or sudden changes in document content. Regularly monitoring your shared documents and access logs can help you identify these signs promptly.
How can I educate my team about security best practices?
+Organize regular security awareness training sessions to educate your team about the latest security threats, phishing attempts, and best practices for secure document sharing. Provide clear guidelines and resources to help them stay vigilant and protect sensitive information.



